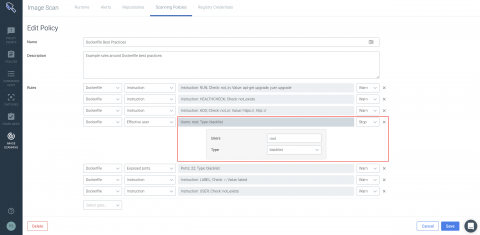
To Agent or Not to Agent: That Is the Vulnerability Management Question
With the evolution of technology comes new approaches to solving problems. Sometimes a new approach fixes the problem; sometimes it creates new ones. The good thing is as folks who work in fast-paced, high-tech environment, we information security professionals are great at quickly analyzing the new technologies and applying them to our daily lives. …Or so we thought!