Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
%term
Is the Private or Public Cloud Right for Your Business?
It wasn’t a very long time ago when cloud computing was a niche field that only the most advanced organizations were dabbling with. Now the cloud is very much the mainstream, and it is rare to find a business that uses IT that doesn’t rely on it for a part of their infrastructure. But if you are going to add cloud services to your company, you will need to choose between the private cloud and the public cloud.
The Myth of a Single Container Security Solution
A proper container security strategy involves evaluating all components in the system.
Big Data in Auditing and Analytics
As organizations seek to evolve their risk management strategies to drive stronger compliance programs, they increasingly seek to automate their compliance documentation. In cybersecurity, however, traditional data collection methods fail since cybercriminals continuously evolve their threat methodologies.
The NIST cybersecurity framework (CSF) and what it can do for you
The NIST Cybersecurity Framework (CSF) has only been around for four years and while developed for critical infrastructure, resulting from Executive Order 13636, it has been widely adopted across both private and public sectors and organizational sizes. It is used inside of the US government, with 20 states using it (at last count).
Detectify opens US office in Boston to accelerate growth
Stockholm, Sweden & Boston, MA – Detectify, a Swedish domain and web application security company, is launching its US operations in Boston, Massachussets. The company achieved 3x revenue growth in 2018 and the launch of the Boston office will further accelerate growth in the US market.
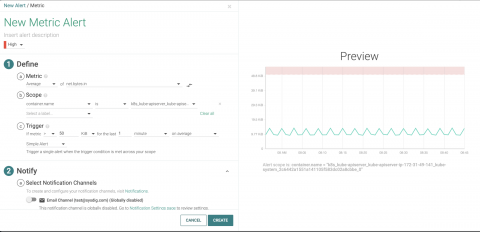
Detecting the Kubernetes API Server DoS Vulnerability (CVE-2019-1002100)
Recently, a new Kubernetes related vulnerability was announced that affected the kube-apiserver. This was a denial of service vulnerability where authorized users with write permissions could overload the API server as it is handling requests. The issue is categorized as a medium severity (CVSS score of 6.5) and can be resolved by upgrading the kube-apiserver to v1.11.8, v1.12.6, or v1.13.4.
How Can You Protect Your Company From Hackers?
Smarter Vendor Security Assessments: Tips to Improve Response Rates
I have been on the receiving end of many vendor security assessments from customers and prospects. Here are some tips to increase the likelihood that you’ll get a timely, usable response to the next vendor security assessment that you send out.
Cybersecurity ROI: An Oxymoron?
Return on investment: is it worth the money? That is the central question both government and industry in deciding on any procurement. Demonstrating ROI on cybersecurity products is notoriously difficult and is one of the underlying reasons for the poor state of our nation’s cybersecurity posture.