Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Networks
Six Tips for Safe Enterprise Networks
Network security is a significant topic that all organizations should consider as a major concern. Regardless of the industry, business, or scope of their operations, all enterprises need to have good network security practices in place to protect against cyberattacks. There are a plethora of different security solutions for different needs, and organizations have to figure out what will work best for them and use the resources that they require.
Log4j/Log4Shell One Year Later: Endemic Vulnerability Indeed
On December 9, 2021, Apache upended the cybersecurity industry by publishing a zero-day vulnerability (CVE-2021-44228) for its ubiquitous Log4j logging utility. Dubbed Log4Shell, the remote code execution flaw (CVSS score:10) allows an attacker to take control of a connected device and run malicious code, access sensitive data or alter its configuration. Because Logj4 is free and easy-to-use, it’s embedded (often deeply) in Java applications used by IT and OT platforms worldwide.
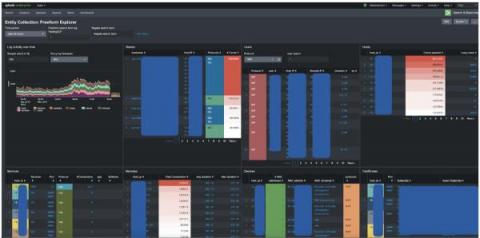
Corelight launches the Entity Collection
Corelight Labs, our amazing research team, has been hard at work on another content collection which we are excited to introduce: the Corelight Entity Collection. Corelight evidence is powerful and comprehensive. So comprehensive, in fact, that it can sometimes be hard to know where to start. Providing customers faster ways to find meaningful context in our data was the driving force behind the creation of the Entity Collection.
The Gift of SSE for your Networking Team
Networking in today’s world is hard enough as it is, especially when connectivity needs to be from everywhere. During this holiday “SSEason,” Axis wants to give the gift of making you and your team’s lives easier. Our new 2022 Atmos Winter Release has some major new features that we hope your networking team and end-users will enjoy!
SANS 2022 Multicloud Survey Exploring the World of Multicloud
SBOMs and the Hunt for Software Supply Chain Vulnerabilities
That’s an excerpt from the fact sheet accompanying the May 2021 Executive Order on Improving the Nation’s Cybersecurity (EO). It refers to one of seven ambitious measures in the EO: shoring up security of that notorious playground for hackers, the software supply chain. Knowing that organizations lack visibility into the components that comprise their connected assets, bad actors can have a field day exploiting vulnerabilities to penetrate networks and take control.
How does VPN Security help in Data Security & Privacy?
Today in a technology-driven business world, network security is an utmost priority for all businesses, especially for those dealing with sensitive data. More so, in an organization that works in a hybrid environment wherein information and critical data are accessed remotely, the need for securing such data and network is important. This has led to a paradigm shift in the approach of establishing a robust security program and security implementations within the organization.