Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Networks
De-Risking Network Automation By Integrating with Itential
Today’s networks are too complex for manual network management and updates. With most enterprises composed of tens of thousands of devices spanning multiple geographical locations, on-premises hardware, Virtual environment, and multiple clouds – it’s virtually impossible to push updates manually. Also – the sheer volume of vendors and coding languages can be overwhelming for a network operations engineer.
Closing the Loop on Automation, Itential and Forward Networks
The Value of Ingesting Firewall Logs
In this article, we are going to explore the process of ingesting logs into your data lake, and the value of importing your firewall logs into Coralogix. To understand the value of the firewall logs, we must first understand what data is being exported. A typical layer 3 firewall will export the source IP address, destination IP address, ports and the action for example allow or deny. A layer 7 firewall will add more metadata to the logs including application, user, location, and more.
New Advanced AlienApps for Fortinet
Here at AT&T Cybersecurity, we feel strongly that security should fit into your business, not the other way around. We lower the friction security brings to day-to-day operations through automating the essential security operations such as detection and response. By integrating different security products together to form a consolidated security architecture, companies can be protected with less effort.
Using Coralogix to Gain Insights From Your FortiGate Logs
FortiGate, a next-generation firewall from IT Cyber Security leaders Fortinet, provides the ultimate threat protection for businesses of all sizes. FortiGate helps you understand what is happening on your network, and informs you about certain network activities, such as the detection of a virus, a visit to an invalid website, an intrusion, a failed login attempt, and myriad others. This post will show you how Coralogix can provide analytics and insights for your FortiGate logs.
Forward Fix LIVE: Network Query Engine
Forward Fix LIVE: Solving Your ACL Problems
Forward Networks' Mathematical Model
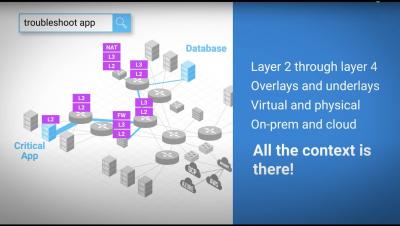
How Your Network Became "The Bermuda Triangle" and How You Can Fix It
“Where’s your app? Where’s your data?” For a long time, if you needed to know where your applications or data were, the answer was clear: it was always either on-premises or in a branch. Universally, almost regardless of organization size, infrastructures were contained, and visible within a defined boundary—you have a data center, a network, a branch, a user.