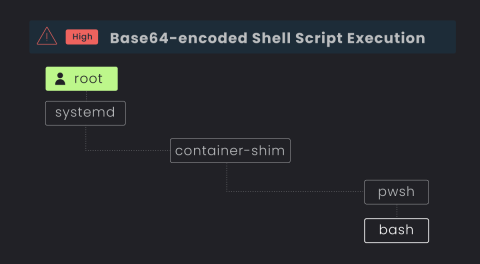
Is Traditional EDR a Risk to Your Cloud Estate?
Organizations are transitioning into the cloud at warp speed, but cloud security tooling and training is lagging behind for the already stretched security teams. In an effort to bridge the gap from endpoint to cloud, teams are sometimes repurposing their traditional endpoint detection and response (EDR) and extended detection and response (“XDR) on their servers in a “good enough” approach.