Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Microsoft 365
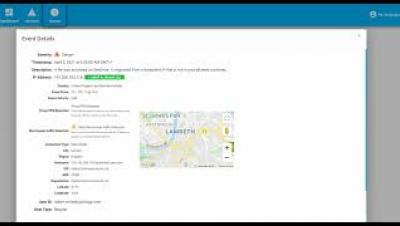
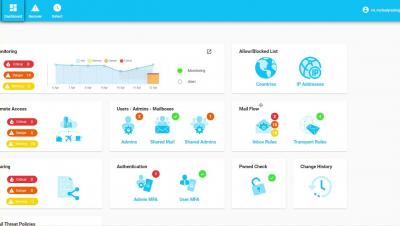
Octiga Office 365 Security Quick Demo
NIST Cybersecurity Framework for Office 365
With more than a decade long history of businesses adopting cloud computing, less than one-third of the enterprises have a documented cloud strategy as per Gartner's estimation. Despite the increased migration to cloud security, we discussed the top cloud security risks that security experts are afraid of today.
Security Trends for Managed IT Service Providers
The global managed security services market was valued at $19.4 billion in 2017 and is forecast to reach $46.1 billion by 2023 at a CAGR of 14.9%. There has been an upward trend seen in the need for threat-intelligence by several sectors today. Due to an increased requirement to fight against the advanced threat landscape, customers today expect managed IT service providers and MSPs to adopt advanced security technologies to detect better and anticipate potential threats well in time.
Top 4 Security Pain Points in Office 365 and their Solutions
According to research by Spanning Cloud, a lack of expertise is one of the most significant issues with the company's Office 365 security and compliance strategy. When referring to Microsoft Office 365 security pain points, it is necessary to understand that the lack of security features in Office 365 is not the issue. The learning curve that follows with these features, is.
Effective Cybersecurity Automation Tools for SMEs who Use Microsoft Office 365
With one in three SMEs adopting cloud-first strategy more than ever, cybersecurity concerns have only grown exponentially. In the wake of the pandemic, nearly 95% of cybersecurity professionals have shown concerns regarding public cloud security. Microsoft Office 365 is at the heart of most small to mid-sized businesses. Combined with a rapid cloud adoption rate, security concerns are not far behind.
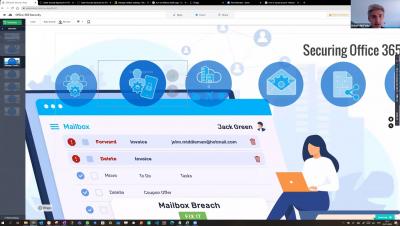
Red Team: O365 MFA Bypass To Device Compromise
The array of phishing vectors used by attackers is constantly expanding. On a daily basis we observe numerous different phishing themes such as voicemails, fake invoices and documents requiring signing. Recently, we have seen more topical themes such as US elections, COVID-19 and Brexit.
Dealing with False Positive Breaches in Universal Audit Log Search in Office 365
Modern cyber security threats have today mutated into a new class that is immune to detection and prevention solutions offered by the security industry. We are looking at this new generation of hackers that master zero-day exploits, credential thefts, fake identities, and developing stealthy malware. These threats have kept the security personnel on their toes, figuring out what the next attack would look like. One of these challenges includes identifying false positive and false negative alerts.