Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Security
Don't Let Malware Hold You Ransom
Ransomware is a relatively new form of malware that poses significant threats to computer networks, even those with effective security systems. It masquerades as legitimate software and uses encryption protocols, like those designed to protect personal information, to lock down files and hold data for ransom. In addition to the increased frequency of attacks, hackers are continuing to grow more sophisticated, targeting high profile businesses that can afford to pay higher ransoms.
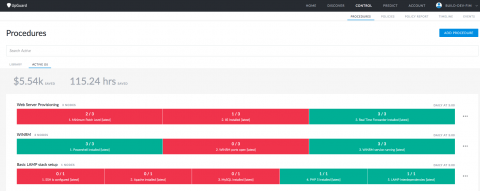
Procedures: Runbook Automation that Works
One of the challenges of building and running information technology systems is solving novel problems. That's where frameworks like scrum and agile come in– getting from the unknown to the known with a minimum of frustration and waste. Another challenge is performing known tasks correctly every single time. Here runbooks, checklists, and documentation are your friend.
6 Steps for Establishing and Maintaining Digital Integrity
To create a secure digital profile, organizations need digital integrity. This principle encapsulates two things. First, it upholds the integrity of files that store operating system and application binaries, configuration data, logs and other crucial information. Second, it protects system integrity to make sure applications, endpoints and networks perform their intended functions without degradation or impairment.
Can Technology Keep Up With Cyber Threats?
What happened when we hacked an expo?
Last year we exhibited at a major information security trade show in London, during the preparation for this we received our exhibitor passes as “print yourself” PDF files. We immediately noticed that there are two forms of barcode here and, interestingly, the QR Code seems quite dense given that all it should be storing is a delegate ID number. Being the inquisitive sort of people that we are, we started up a QR scanner and had a look at its contents.
How Technology Protects Against Wrongful Termination Claims
Using technology to protect your company from wrongful termination claims
7 Questions for Evaluating your Security Posture against Insider Threats
Insider threats top the list of the most dangerous cyber risks for organizations worldwide. It doesn’t take much effort for insiders to steal your sensitive data, while such activities are hard to discover and impossible to prevent. Unfortunately, lack of visibility into user behavior is one of the key reasons why companies suffer from data breaches that involve either human negligence or malicious intent.
Data Security Considerations for Your Work From Home Policy
Incorporating data security in your work from home policy
Securing Data Storage With UpGuard
Despite spending billions on cybersecurity solutions, private industry, government and enterprises alike are faced with the continued challenge of preventing data breaches. The reason cybersecurity solutions have not mitigated this problem is that the overwhelming majority of data exposure incidents are due to misconfigurations, typically by way of third-party vendors, not cutting-edge cyber attacks.