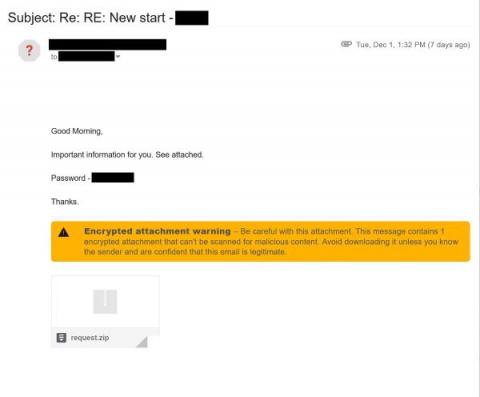
Announcing Veracode in AWS Marketplace: Streamlining Secure Software Development for AWS Customers
Digital transformation continues to accelerate, and with it, businesses continue to modernize their technological environments, leveraging developer-first cloud-native solutions to build, host, and secure their software. At Veracode, we continue to see customers leveraging large cloud providers, such as AWS, as a central platform to conduct these activities.