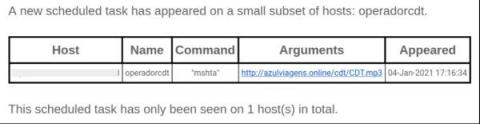
Stay Alert to Security With Xray and PagerDuty
When it comes to securing your software development against open source vulnerabilities, the earlier action occurs — by the right person — the safer you and your enterprise will be. Many IT departments rely on the PagerDuty incident response platform to improve visibility and agility across the organization.