Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Security
Netskope Threat Coverage: 2020 Tokyo Olympics Wiper Malware
Major sporting events, like the World Cup or the Olympics, are usually targets of cybercriminals that take advantage of the event’s popularity. During the 2018 World Cup, for example, an infected document disguised as a “game prediction” delivered malware that stole sensitive data from its victims, including keystrokes and screenshots.
Securing Access to Your MongoDB Database
MongoDB is one of the most popular open-source databases. Unfortunately, this also means ubiquity of misconfigured and unsecured MongoDB deployments out in the wild. Just in recent years, we’ve seen several hacks involving thousands of MongoDB databases left exposed online without any protection, making them ripe for the hacker’s picking. It doesn’t have to be this way, though.
Encrypted Traffic Collection
Proactive security using Open NDR with Zeek
Splunk Security Cloud
Phishing Attacks Often Target Small Businesses - Here's What to Watch for
Scammers target businesses with phishing emails all the time, pretending to be legitimate customers or vendors asking for payment. While any company can be vulnerable to this type of attack, small- to medium-size companies are particularly vulnerable because it is easier for a scammer to do a bit of research online and identify the right people to impersonate or send a phishing email to.
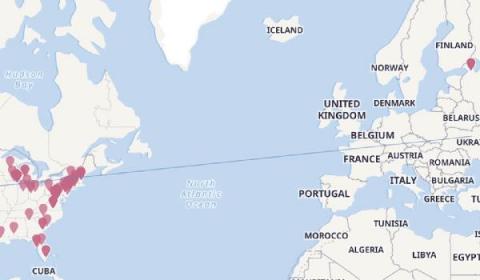
Detecting unusual network activity with Elastic Security and machine learning
As we’ve shown in a previous blog, search-based detection rules and Elastic’s machine learning-based anomaly detection can be a powerful way to identify rare and unusual activity in cloud API logs. Now, as of Elastic Security 7.13, we’ve introduced a new set of unsupervised machine learning jobs for network data, and accompanying alert rules, several of which look for geographic anomalies.