Detecting and mitigating CVE-2022-26134: Zero day at Atlassian Confluence
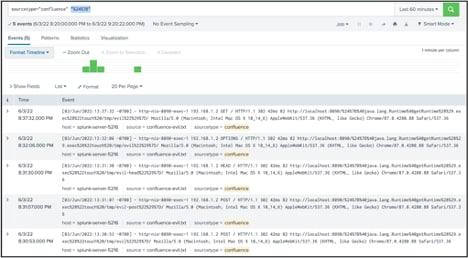
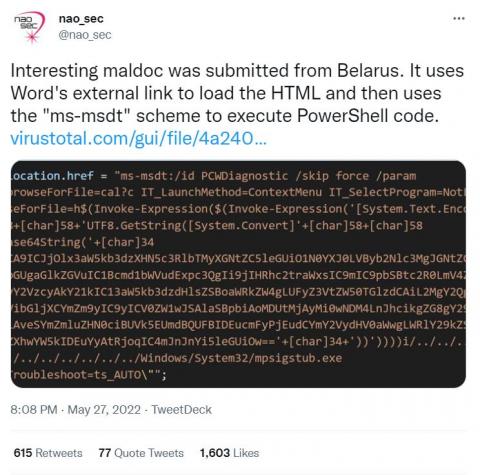
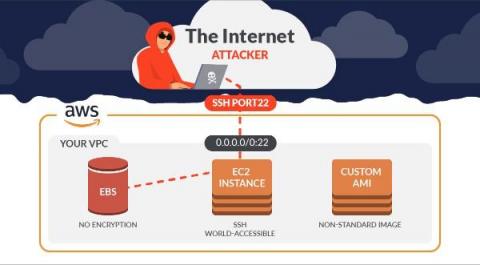
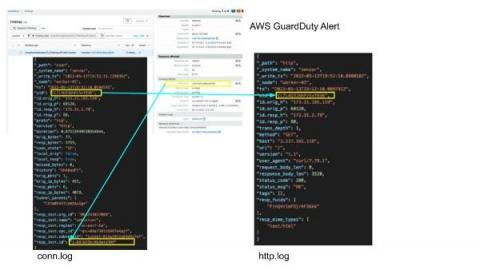
A new zero day vulnerability actively exploited in the wild has been found in Atlassian Confluence. The vulnerability CVE-2022-26134 affects all supported versions of Confluence Server and Confluence Data Center allowing an unauthenticated user to run arbitrary commands remotely. The Atlassian team confirmed the vulnerability with an official tweet and then also published a security advisory to update its customers.