Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Security
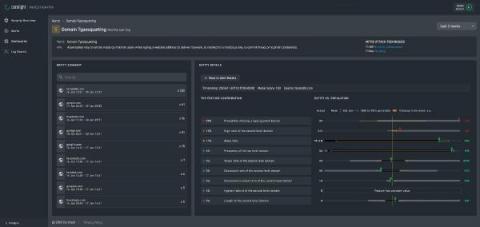
Multivariate Anomaly Detection: Safeguarding Organizations from Internal Threats
The term “internal threat” refers to the risk that somebody from inside a company could exploit a system to cause damage or steal data. Internal threats are particularly troubling, as employees may abuse extended privileges, leading to massive losses for the organization. One such infamous case is of an ex-Google employee who was charged with theft of trade secrets from Google for a ride-hailing start-up Uber.
Healthcare under attack: an overview
Corelight Investigator introduces new Machine Learning Models
Corelight Investigator furthers its commitment to delivering next-level analytics through the expansion of its machine learning models. Security teams are now enabled with additional supervised and deep learning models, including: We continue to provide complete transparency behind our evidence -- showing the logic behind our machine learning models and detections, allowing analysts to quickly and easily validate the alerts.
Microsoft Power Platform DLP Bypass Uncovered- Finding #1
Hello everyone! I’m Yuval Adler, Customer Success Director at Zenity. I’m inviting you to read my blog series where I share new Microsoft Power Platform DLP Bypass findings we uncovered.
Ultimate Guide to OWASP API Top 10
The OWASP API Top 10 is a list of common vulnerabilities found in APIs. OWASP created it as a resource for developers, testers, and security professionals to help them understand how to protect against API threats. Many people think that APIs are just another type of web application, but they're not; they have their own set of risks and challenges that need to be addressed. A simple API call can result in a data breach that could have lasting consequences for your business.
Introducing the LimaCharlie Query Language (LCSQL) BETA
Stories from the SOC - RapperBot, Mirai Botnet - C2, CDIR Drop over SSH
Since mid-June 2022, AT&T Managed Extended Detection and Response (MXDR) Security Operations Center (SOC) observed an enormous number of attacks from Mirai botnet-C2 attempting to gain access to SSH servers instead of Telnet.Due to the various tactics, techniques, and procedures (TTP) observed, this attack has been associated with RapperBot botnet (Mirai variants.) RapperBot’s goal is still undefined.
Royal Mail Ransomware Attack - Part 2
Following on from part 1 of our Royal Mail blog, our consultants take a more technical approach to the Royal Mail Ransomware attack and dive deeper into what happened.
The benefits of outsourced Data Protection Officer as a Service
As the world becomes increasingly digital and cloud based, the importance of data protection and privacy has become paramount for all organizations. One key aspect of ensuring compliance with data protection laws and regulations is the appointment of a Data Protection Officer (DPO). However, appointing a DPO internally can present several challenges, including conflicts of interest and a lack of specialized skills. That is where Data Protection Officer as a Service (DPOaaS) comes in.