Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Security
Incident Response Service Breakdown
Incident response is a comprehensive approach to dealing with potential security incidents, such as unauthorised access, data breaches, and malicious attacks that might affect an organisation’s network. The goal of incident response is not just to contain the threat but also to learn from it by understanding what happened, why it happened, and how it can be prevented from happening in the future.
Threat Hunting vs Incident Response for Cyber Resilience
The State of Data Security: The Hard Truths of Data Security from Rubrik Zero Labs
Rubrik Zero Labs is excited to debut its second State of Data Security report: “The State of Data Security: The Hard Truths.” This in-depth global study is the first public use of Rubrik telemetry data to provide objective data security insights. Rubrik data is complemented by an extensive third-party study conducted by Wakefield Research, which provides a deeper look into the challenges IT and security decision-makers face, the impacts of these challenges, and possible solutions.
Blumira speeds time to market by building with LimaCharlie
Like all cybersecurity providers, Blumira has had to respond to the rise of remote and hybrid work models. But given Blumira’s focus on SMBs and mid-market companies, they found many businesses in their target market priced out of mature endpoint monitoring solutions—or without the technical ability and infrastructure to run the endpoint agents a larger organization might use.
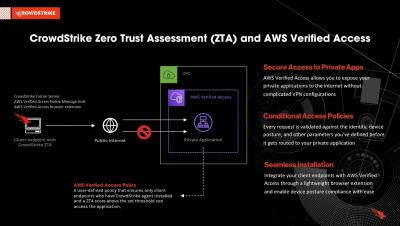
Securing private applications with CrowdStrike Zero Trust Assessment and AWS Verified Access
Candid Chats - Can you cheat Cyber Essentials?
Candid Chats: What's the big deal about PCI DSS v4?
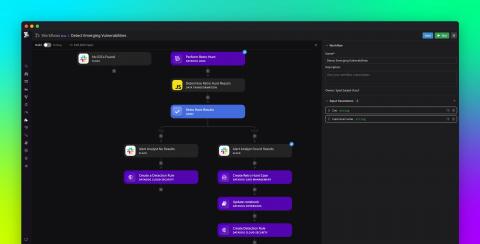
Automate common security tasks and stay ahead of threats with Datadog Workflows and Cloud SIEM
Detecting and remediating security threats is a constantly evolving concern for modern DevSecOps and security operations center (SOC) teams. Moreover, manually investigating and responding to vulnerabilities and threats is time-consuming, laborious, and knowledge-intensive.
164% increase in tax-related phishing emails since February 2023
Ahead of US Tax Day on April 18, 2023, attackers are taking the opportunity to send finance-related phishing attacks. There has been a 164% increase in tax-related phishing emails since February 2023 and a 32% increase versus 2022 levels. Typically in these attacks, cybercriminals attempt to convince victims that they have a tax refund available or have underpaid their taxes, when in reality, the email contains a malicious link or attachment.