Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Blog
I resent my Email and my invite
Here is a short communication tip that may help you in your daily interactions. How often have you “resent” an E-Mail? How often have you told a person that you will “send an invite”? You may be wondering why I am bringing this up in a post usually reserved for cybersecurity. Am I just being overly pedantic? Am I just a rigid grammarian? One could easily assert that (and my friends do so all the time, so feel free to jump on that bandwagon).
How to prevent elder abuse and financial fraud
The elderly population in the U.S has been on a steady incline for the past few decades. With more seniors living longer new challenges arise. Unfortunately, many seniors become vulnerable to different types of abuse, neglect, and exploitation as they age. The National Council on Aging estimates that financial fraud and abuse against seniors costs older Americans up to $36.5 billion each year.
Improving WordPress plugin security from both attack and defense sides
Paul is a front- & backend developer with a passion in security, who creates designs occasionally. After starting out with WordPress plugin vulnerabilities, he joined the bug bounty world and now also a white hat hacker in the Detectify Crowdsource community. As he has acquired his knowledge through community resources himself and wants to make the internet a safer place, he shares his know-how to give something back and in this case tips on WordPress plugin security.
Looking for Love in All the Wrong Places - AKA, the Cyber Security Talent Shortage
The subject of the cyber security talent shortage has been over-reported to the extent that no one wants to talk about it anymore. Even more than that, the only solution that really ever gets mentioned is developing more university cyber programs. But that solution is dead wrong—or at least it misses the crux of the issue completely.
Governors Association Says States Need Cyber Disruption Response
On July 11, 2019, the National Governors Association released a new publication on the topic of cyber disruption response plans across America. The report examines state cyber disruption response plans, providing recommendations for state officials who want to create or review their own response plans.
Prevent Wordpress hacking using this Pen Testing guide
Welcome back to the next edition of “Hacking WordPress”. Find Part 1 if you missed it. Let me start with a PSA message. It is illegal to hack, log in to, penetrate, take over or even hack, a system or network of systems without the explicit permission of the owner. Criminal hacking is illegal and punishable under Federal Law. I am describing methods to learn more about WordPress so you can protect your sites better.
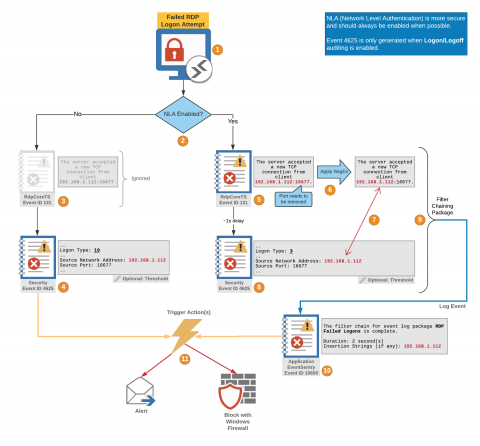
RDProtector: Automatically blocking malicious IPs from RDP with EventSentry
The recently discovered BlueKeep RDP vulnerability reminds us yet again (as if needed to be reminded) that monitoring RDP is not a luxury but an absolute necessity. Many organizations still expose RDP ports to the Internet, making it a prime target for attacks. But even when RDP is only available internally it can still pose a threat – especially for large networks.
Using AWS Session Manager with Enhanced SSH and SCP Capability
Amazon Web Services recently announced new capabilities in the AWS Systems Manager Session Manager. Users are now capable of tunneling SSH (Secure Shell) and SCP (Secure Copy) connections directly from a local client without the need for the AWS management console. For years, users have relied on firewalls and bastion hosts in order to securely access cloud assets, but these options have security and management overhead tradeoffs.
The 4 Questions Industrial CISOs Need to Ask When Evaluating a Cybersecurity Tool
Cybersecurity is finally reaching the shop floor in earnest thanks to new technology that works with—not against—the legacy equipment that runs most industrial control systems (ICS). That being said, industrial companies and organizations in sectors like manufacturing, energy, utilities, transportation and water treatment can be slow to adapt to the new cybersecurity tools at their disposal because they present a new way of operating in an industry that’s set in its ways.