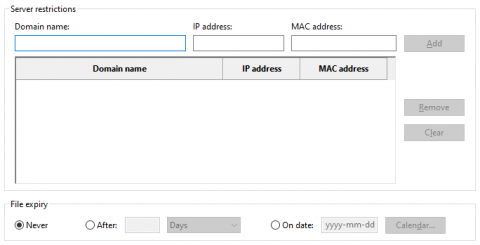
Simplifying Secure Server Access with Teleport's Approval Workflow
Back in the early 2010s, a Forrester researcher, John Kindervag, noticed that corporations had a binary view of trust and privilege. Once new employees have completed training, they are given full access to all the tools and VPNs needed to get their job done. Once they are logged on, they are trusted completely. Kindervag noticed that “trust” is a vulnerability that can be exploited. Since then, awareness of Zero Trust implementations has grown, in particular Google’s BeyondCorp.