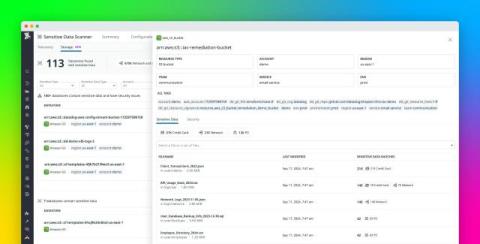
Discover sensitive data in your cloud data stores with Sensitive Data Scanner
When engineering teams move their workloads to the cloud, it’s often possible that sensitive data—such as credit card numbers, login credentials, and personally identifiable information (PII)—unintentionally moves to the cloud with them. To secure this data, avoid costly breaches, and meet GRC requirements, these teams often catalog where this data is stored and establish the right controls to limit access.