Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
%term
Data Protection Officer (DPO)
A Data Protection Officer (DPO) is a role that oversees a company’s processing of personal data of staff, customers or any other data subjects to ensure it is done in accordance with the relevant data protection laws. A DPO effectively acts as a bridge between your company and data subjects as well as the ICO (or relevant regulatory authority).
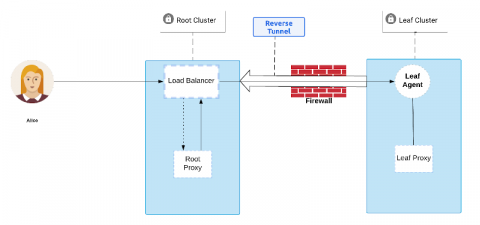
Greed is Good: Creating Teleport's Discovery Protocol
This article will be exploring the challenges Gravitational engineers faced when designing a discovery protocol for Teleport and how we learned to channel our inner Gordon Gekko to create a greedy solution. Teleport helps to empower engineers by enabling remote, secure access to their infrastructure while meeting compliance requirements, reducing operational overhead and complete visibility into access and behaviors.
What is a Third-Party Vendor?
A third-party vendor is any entity that your organization does business with. This includes suppliers, manufacturers, service providers, business partners, affiliates, brokers, distributors, resellers and agents. Vendors can be upstream (suppliers and vendors) and downstream (distributors and resellers), as well as non-contractual entities.
Thunder on the Horizon: 4 Security Threats for the Cloud
Security is both a benefit and a concern for enterprises when it comes to cloud computing. On the one hand, Datamation found in its State of the Cloud, 2019 survey that many organizations are moving to the cloud because they found that cloud-service providers (CSPs) offer better all-around security than they could achieve by themselves.
Top 10 best practices of Cloud SIEM
What is an Attack Vector? Common Attack Vectors
In cybersecurity, an attack vector is a path or means by which an attacker can gain unauthorized access to a computer or network to deliver a payload or malicious outcome. Attack vectors allow attackers to exploit system vulnerabilities, install different types of malware and launch cyber attacks. Attack vectors can also be exploited to gain access to sensitive data, personally identifiable information (PII) and other sensitive information that would result in a data breach.
Escaping the Egregious Eleven - Part One
Helping to define and examine the top perceived cloud security threats of the day, the ‘Egregious Eleven’ is the most recent iteration in an evolving set of summary reports published by the Cloud Security Alliance (CSA). It follows on from the ‘Treacherous Twelve,’ which they defined for us in 2016, and the ‘Notorious Nine,’ which they presented in 2013.
Do Files Matter to your Business?
Do Files Matter? As Chief Customer Officer of Egnyte, I get to meet many of our customers and influencers. This is immensely invigorating for two reasons – it helps me get our POV out to the market in an old school, door to door sort of way but more importantly, keeps me on an arc of continuous learning to shape our approach to the market. While this process has played out well over the last several years I have simply run out of time to meet everyone as Egnyte grows.