Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
%term
What is the SHIELD Act?
The New York Stop Hacks and Improve Electronic Data Security Act (SHIELD Act) or Senate Bill 5575, was enacted on July 25, 2019 as an amendment to the New York State Information Security Breach and Notification Act. The law goes into effect on March 21, 2020. The motivation behind the SHIELD Act is to update New York's data breach notification law to keep pace with current technology.
The Importance of Third-Party Vendor Risk Management for the Banking Industry
Today’s banks and financial institutions closely cooperate with various third-party vendors. While such cooperation brings a lot of benefits, it also raises some significant concerns regarding the security of the data and resources these vendors have access to. In fact, according to Verizon’s 2019 Data Breach Investigations Report, the financial sector is among the most targeted, accounting for about 10% of all data breaches across all industries in 2018.
The Outcomes of SIEM and SOAR in 2019 (Part 1)
Like the previous years, 2019 also witnessed the surge in data breaches and cyber-attacks. However, organizations having SIEM or/and SOAR system in place were better than those using traditional security tools. The cyber-attacks in 2019 were mostly related to financial crimes, supply chain attacks, phishing exploits, state-sponsored attacks, Grid attacks, health sector attacks, and attacks on IoT devices. Cybersecurity skills shortage was also one of the major concerns in 2019.
What to expect from a penetration testing report
Penetration testing (or pen testing) should form a crucial part of every cyber security strategy, but to get the most value from assessments, organisations need to ensure that they receive the best quality reports from providers.
CVE-2020-0601 - How to operationalize the handling of vulnerabilities in your SOC
Software vulnerabilities are part of our lives in a digitalized world. If anything is certain, it’s that we will continue to see vulnerabilities in software code! Recently the CVE-2020-0601 vulnerability, also known as CurveBall or “Windows CryptoAPI Spoofing Vulnerability”, was discovered, reported by the NSA and made headlines. The NSA even shared a Cybersecurity Advisory on the topic. Anthony previously talked about it from a public sector and Vulnerability Scanner angle.
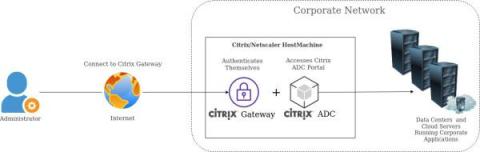
The Citrix Vulnerability And What It Means For You
In December 2019, Citrix announced that their flagship product, Citrix Application Delivery Controller (ADC) and Gateway, had a vulnerability that would allow code execution to take place on affected devices without any authentication. This vulnerability (designated CVE-2019-19781) was severe - on a scale of 1 to 10 it was deemed a 9.8 meaning that an attacker able to exploit this vulnerability could do serious damage.
Automated Penetration Testing: 5 Benefits for CISOs
Research by Cybersecurity Ventures projects a doubling of the global cost of cybercrime in the 2015-2021 period from $3 trillion to $6 trillion. The escalation of cybercrime is closely related to the rapid expansion of the cyber attack surface. For instance, the total number of Internet users doubled between 2015 and 2018 from 2 billion to 4 billion, and is expected to hit 6 billion by 2022.
NIS Directive: Who are the Operators of Essential Services (OES)?
The NIS Directive is the first EU horizontal legislation addressing cybersecurity challenges and a true game-changer for cybersecurity resilience and cooperation in Europe. The Directive has three main objectives. The NIS Directive is the cornerstone of the EU’s response to the growing cyber threats and challenges which are accompanying the digitalization of our economic and societal life.
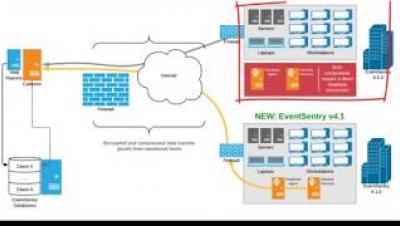
You've Bought Security Software. Now What?
Many years ago when I first started my career in network security as a support engineer, I received a phone call from a customer. (Let’s call him “Frank.”) He used our vulnerability scanner as a consultant for his own customers, and he was concerned that the scanner came back with 0 results. After reviewing his set-up, I easily discovered the answer.