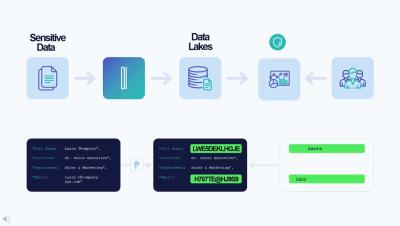
Advanced Android Malware Targets NFC Data for ATM Cashouts
A new strain of Android malware has emerged, targeting victims' card details and utilizing near-field communication (NFC) technology to facilitate unauthorized ATM withdrawals. This sophisticated crimeware, active since March 2024, has already impacted customers of three major Czech banks.