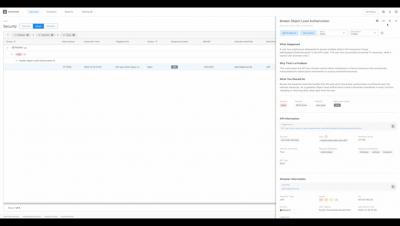
What is an Attack Vector?
Attack vectors are the techniques attackers deploy to infiltrate or breach your network. Certain attack vectors take aim at humans that have network access, while other attack vectors target weaknesses in overall infrastructure and security. If this video doesn't cover everything you need to know, you can learn more about attack vectors at our Noname Academy: nonamesecurity.com/learn/what-is-an-attack-vector/