CrowdStrike Falcon Go Demo
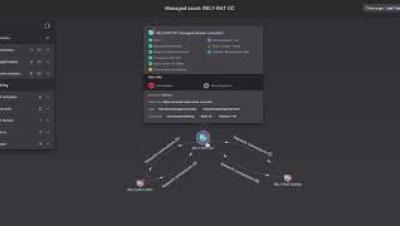
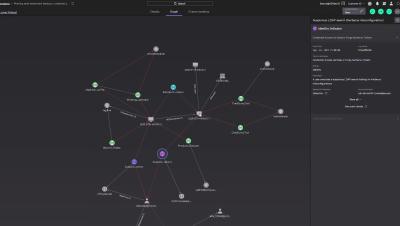
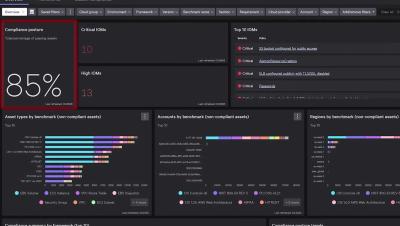
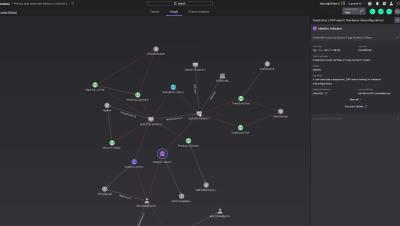
Next-generation security is simplified with CrowdStrike Falcon Go. Purpose-built for small and medium businesses, Falcon Go replaces your legacy antivirus with award winning, AI-powered security trusted by thousands of businesses. Falcon Go's simple operation, management, and deployment enables your business to stop breaches. Next-generation security for small and medium businesses: that's Falcon Go.