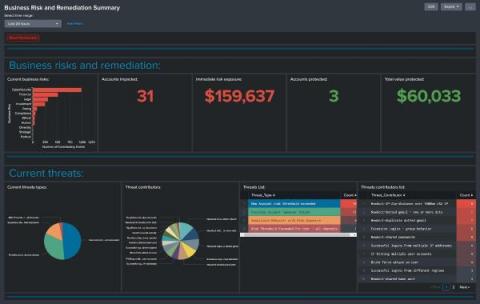
Detect Fraud Sooner with the Splunk App for Fraud Analytics
It will not come as a surprise to you that fraud and financial crime is continuing to challenge organizational business and cyber resiliency plans. Odds are you have dealt with fraud firsthand, or know someone experiencing the pains caused by fraud. Back in 2020 we shared some thoughts about how we believe leveraging a data platform like Splunk can help you gain more anti-fraud value and insights from your data and showed how you can determine what your data is worth.