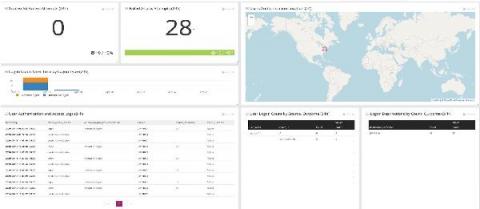
Integrating With ServiceNow for a Single Source Of Truth
Network operations teams rely on highly specialized tools developed by individual vendors designed to address particular problems. The result? Most enterprises have 10+ Network Operations applications in place and they don’t talk to each other—which means that network operations engineers spend an exhaustive and unnecessary amount of time toggling between applications and sifting through information as they work to resolve tickets.