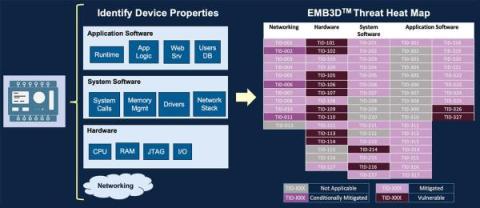
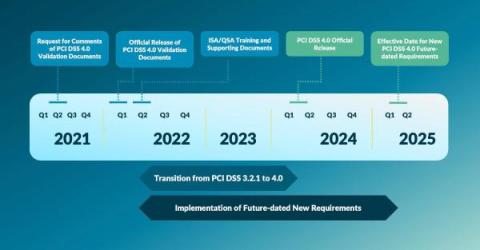
Securing the unseen: MITRE's EMB3D framework for embedded devices
The security of embedded devices is in the news over the last few years, especially IoT assets and OT systems. From connected medical devices to industrial control systems to smartwatches and building automation, connected IoT devices will expand to over 25 billion by 2028.