Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Latest News
Using BPF to Transform SSH Sessions into Structured Events
Teleport 4.2 introduced a new feature called Enhanced Session Recording that takes an unstructured SSH session and outputs a stream of structured events. It’s the next step in Teleport’s evolution that uses new technology (eBPF or now simply known as BPF) to close some gaps in Teleport’s audit abilities. Below you can see an illustration of this feature and if you keep reading, we’ll get into some of the technical details.
What is the Consensus Assessments Initiative Questionnaire (CAIQ)?
The Consensus Assessments Initiative Questionnaire (CAIQ) is a security assessment provided by the Cloud Security Alliance (CSA) for cloud consumers and auditors to assess information security capabilities of cloud providers.
Red Teaming: How to Run Effective Cyber-Drills?
What is red teaming? How is it different from conventional penetration testing? Why do we need blue, red, and white teams? How are cyber-drills carried out, and what results should be expected? In this article, we will answer these and other questions related to red teaming.
Business Continuity With Egnyte For Those Impacted by Coronavirus
The COVID-19 virus (or coronavirus) is having an impact on businesses across the globe. Organizations have been pressed to balance productivity with the protection of their employees and partners. With that in mind, we’ve collected a few helpful resources from Egnyte that can help enable continuity in times of business disruption.
What is really an API?
API has become one of those catch-all terms that developers throw around without really considering the context. On any given week, you will come across discussions like "How to use the Twitter API", "New framework X is great because it has a low API surface", and "Best practices for building an API." Is an API a data source? Is it a service? Is it a way to call native functionality? The truth is, in modern software development it can mean any of these things.
Inherent Risk vs. Control Risk: What's the Difference?
Inherent risk and control risk are two of the three parts of the audit risk model, which auditors use to determine the overall risk of an audit. Inherent risk is the risk of a material misstatement in a company’s financial statements without considering internal controls.
Gehaxelt - How Wordpress Plugins Leak Sensitive Information Without You Noticing
Sebastian Neef (@gehaxelt) is a IT security freelancer and a top contributor from the Detectify Crowdsource community. In this guest blog, he looks at ways WordPress plugins leak sensitive data in the wild: The OWASP Top 10 puts Sensitive Data Exposure on the 3rd place of the most common web security issues. In this blog post we will have a look at sensitive data exposure that you might not be aware of.
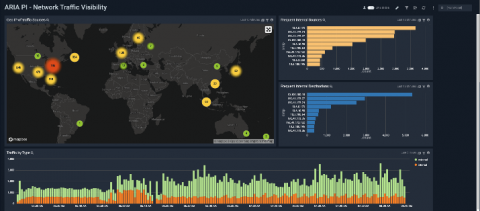
A New Integration between Sumo Logic and ARIA Cybersecurity Solutions
NSA Releases Cloud Vulnerability Guidance
The United States’ National Security Agency (NSA) has put together a short guidance document on mitigating vulnerabilities for cloud computing. At only eight pages, it is an accessible primer for cloud security and a great place to start before taking on something like the comprehensive NIST 800-53 security controls.