Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Latest News
One in Four Gen Z and Millennial Consumers Buy with Bots
Bridging Theory and Practice through Cybersecurity Education
CrowdStrike Brings AI-Powered Cybersecurity to Small and Medium-Sized Businesses
Cyber risks for small and medium-sized businesses (SMBs) have never been higher. SMBs face a barrage of attacks, including ransomware, malware and variations of phishing/vishing. This is one reason why the Cybersecurity and Infrastructure Security Agency (CISA) states “thousands of SMBs have been harmed by ransomware attacks, with small businesses three times more likely to be targeted by cybercriminals than larger companies.”
Financial Institutions in New York Face Stricter Cybersecurity Rules
Boards of directors need to maintain an appropriate level of cyber expertise, incidents must be reported within 72 hours after determination, and all ransom payments made must be reported within a day. Those are just some of the changes made by The New York State Department of Financial Services to its Cybersecurity Requirements for Financial Services (23 NYCRR 500), effective November 1, 2023.
Secure Access Control in 2024: 6 Trends to Watch Out For
Secure access control, part of the broader field of user management, is a key concept in the realm of information security, particularly in the business environment. It refers to the process of selectively restricting and allowing access to a place or resource. In the context of information technology, it is a vital element of data protection, dictating who or what can view or use specific resources in a computing environment.
3 Considerations to Make Sure Your AI is Actually Intelligent
In all the hullabaloo about AI, it strikes me that our attention gravitates far too quickly toward the most extreme arguments for its very existence. Utopia on the one hand. Dystopia on the other. You could say that the extraordinary occupies our minds far more than the ordinary. That’s hardly surprising. “Operational improvement” doesn’t sound quite as headline-grabbing as “human displacement”. Does it?
Snyk achieves AWS Security Competency
We are thrilled to announce that Snyk, a leading provider of cloud native application security solutions, has achieved the prestigious AWS Security Competency status. The AWS Security Competency validates Snyk's deep security expertise and commitment to delivering a comprehensive application security solution for modern organizations building and running their applications on the Amazon Web Services (AWS).
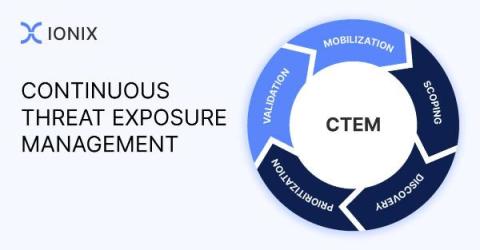
Gartner CTEM Starts with EASM
External Attack Surface Management(EASM) has emerged as a cybersecurity gold standard – a core component of modern cybersecurity programs. As digital organizations have grown more complex, getting the whole picture of the external attack surface – what’s connected to what and how this could pose danger – is a maze that only-world-class EASM solutions have been able to successfully navigate.
Trustwave Threat Intelligence Briefing: The 2023 Retail Services Sector Threat Landscape
The holiday shopping season is teed up for its annual explosion of spending. Retailers know this, consumers know this, cybercriminals know this, and are unfortunately ready to take advantage of any weak link that can be found to steal vital consumer and business data. However, unlike gift buyers heading to stores or shopping online on Black Friday and Cyber Monday, these adversaries are not seasonal actors.