Six steps for running a successful security program
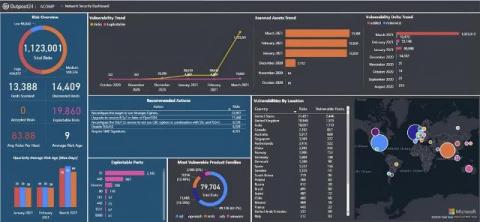
Starting a security program can be challenging for some organizations, especially running a mature program across a large business. Resourcing, lack of organization, and not having a clear remediation strategy are key aspects to the failure of some programs, which can all result in severe breaches of businesses. I’ll walk through seven steps that will help ensure your program is a success and also give a quick overview of how Outpost24’s Managed Services can support your efforts.