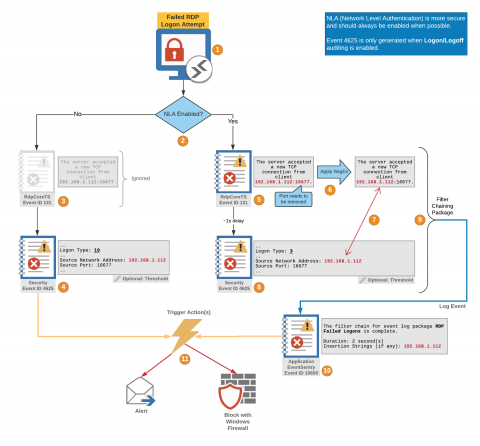
RDProtector: Automatically blocking malicious IPs from RDP with EventSentry
The recently discovered BlueKeep RDP vulnerability reminds us yet again (as if needed to be reminded) that monitoring RDP is not a luxury but an absolute necessity. Many organizations still expose RDP ports to the Internet, making it a prime target for attacks. But even when RDP is only available internally it can still pose a threat – especially for large networks.