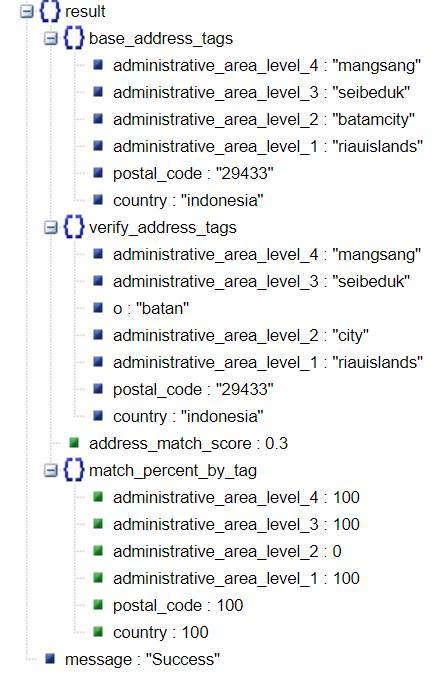
Product Update: Address Net Model for Address Verification
Complex address systems and its verification have continued to be a big riddle for technology companies. Currently address verification is done manually by matching the address mentioned in the identity document with the address filled in any kind of application form filled by the customer.