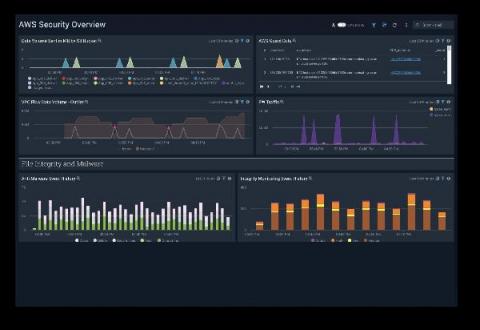
Snyk named Visionary in 2021 Gartner Magic Quadrant for AST
We have more than a few reasons to be thrilled with the results of the 2021 Gartner Magic Quadrant for Application Security Testing. In our debut on the report, Snyk has been recognized as a Visionary. Additionally, we are placed furthest in the Visionaries quadrant for both Completeness of Vision and Ability to Execute, and second-furthest for Completeness of Vision in the overall Magic Quadrant.