Keep infrastructure as code secure with Synopsys
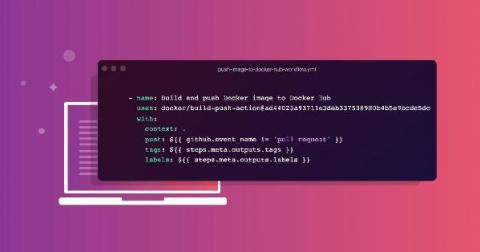
Infrastructure as code is a key concept in DevOps for cloud deployments. Learn how to secure it using Rapid Scan SAST. It was not long ago when we needed to submit an IT support ticket to help launch infrastructure configurations (virtual machines, networks configurations, load balancers, databases, etc.) every time we needed to deploy a new application. It worked when we needed those less frequently, but it was not easily scalable.