Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Latest News
What is Ransomware-as-a-Service (RaaS)?
News of ransomware attacks disrupting supply chains has increased recently. As threat actors disrupt businesses and critical infrastructure, they may appear to be working harder. However, cybercriminals treat ransomware as a business, enabling an underground industry. Ransomware-as-a-Service (RaaS) is a growing underground industry that continues to place sensitive information at risk.
Everything You Need to Know About Neo Bank Security
Of all the modern business ecosystems, the Fintech sector is one of the most volatile landscapes that is teeming with industry and technological disruptions. And, adding to the pre-existing list is Neobanking. Currently, there are 246 neo banks in the world, and the market projections suggest an annual average growth rate (CAGR) of 47.7 percent until 2028, amounting to 722.6 billion U.S. dollars.
The meaning behind XDR: A beginner's guide to extended detection and response
In the world of threat detection and response, alert fatigue and tool sprawl are real problems. Security professionals are struggling to manage different tools and control points and still relying on manual processes, which results in security that is fragmented and reactive. Analysts need better visibility and control, more context, and better use of automation so they can cut through the noise and respond to threats faster and more effectively.
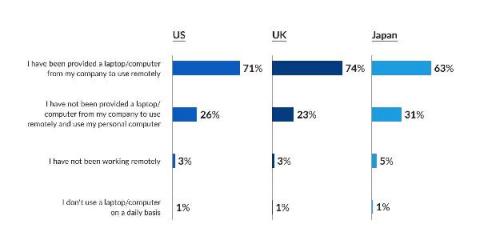
2021 SecureAge COVID & cybersecurity study
In 2021 SecureAge surveyed 1,000 US-based respondents (400+ employers; 600+ employees), 600 UK-based respondents (200+ employers; 400+ employees), and 300 Japan-based respondents (100+ employers; 200+ employees) to find out more about cybersecurity concerns during the pandemic and what has been done to prepare for the future. The study, conducted between July and August 2021, revealed new cybersecurity trends as well as how businesses have and have not adapted.
Arctic Wolf's Global Survey Reveals Lack of Confidence in Cybersecurity Defenses and Government Action
After a year of high-profile cyberattacks and uncertainty caused by the extended pandemic, Arctic Wolf wanted to understand the impact this period has had on cybersecurity strategy and business overall. In August of this year, we commissioned a survey of over 1,400 senior I.T. decision-makers and business executives in the U.S., U.K., and Canada, and today we are publishing the results.
BazarLoader: Using LoLBins through Office Documents to Deliver Payloads
Malicious Microsoft Office documents are a popular vehicle for malware distribution. Many malware families such as Emotet, IcedID, and Dridex abuse Office documents as their primary distribution mechanism. Attackers have long used phishing emails with malicious Microsoft Office documents, often hosted in popular cloud apps like Box and Amazon S3 to increase the chances of a successful lure. The techniques being used with Office documents are continuing to evolve.
Do We Still Need a Bastion?
There is a growing discussion among network engineers, DevOps teams, and security professionals about the security benefits of bastions. Many assume that they are the “old way” of network access and have little relevance in the modern cloud native stack. These speculations are not irrelevant as in recent years, the corporate IT network perimeter as we knew it is diminishing, and the concept has been shifted to data, identity, and compute perimeter.
Lookout is Collaborating With the U.S. Government on a New Vision for Zero Trust
In early 2020, almost every government agency embraced telework in response to the pandemic. With telework, employees operate outside the security perimeter that was put in place to protect them and the agency’s data. As a result, telework has had significant cybersecurity ramifications. Lookout has a long history of collaborating with the public sector to secure agency employees.
CIS Control 5: Account Management
Knowing who has credentials, how those credentials are granted, and how they are being used is the foundation of any secure environment. It begins with user accounts and the credentials they use. Maintaining a thorough inventory of all accounts and verifying any changes to those accounts as authorized and intentional vs unintended is paramount to establishing a secure environment and this includes service accounts.