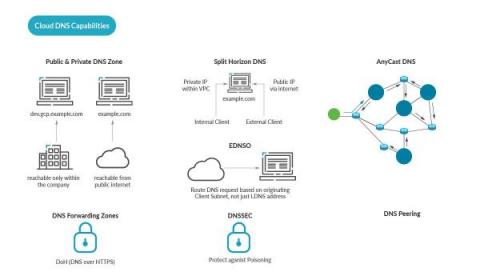
Cloud DNS Security - How to protect DNS in the Cloud
When using DNS in the Cloud, security cannot be forgotten. This article is for cloud architects and security practitioners who would like to learn more about deployment options to DNS security and security best practices for DNS in the Cloud. You will learn DNS best practices for DNS security, and see the advantages of a cloud approach for DNS. The three main requirements for DNS are: In this article, we begin with DNS basics, then move on to the topic of DNS in the Cloud.