Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Latest News
Lets Talk Bank Fraud - How to Protect Your Bank Details
Bank fraud is a type of financial crime that involves the use of false representations and illegal activities to obtain money or other assets from a financial institution. It can involve forging signatures, using stolen bank account numbers, or using fake documents to gain access to funds.
External Attack Surface Management Market Size: An Overview
Attack surface management (ASM) is becoming increasingly important for businesses today. The attack surface is expanding and becoming more complex than ever before, driven by numerous factors, including the COVID-19 pandemic and resulting shift to remote work, widespread cloud adoption and the resulting growth of shadow IT, increased use of managed services (SaaS), and third-party vendor services.
AI and Cybersecurity: Some observational implications of the intersection between the two
There is a possibility that artificial intelligence (AI) will have a significant influence, in either a good or bad direction, on cybersecurity. On the plus side, artificial intelligence (AI) can be used to automate and improve many parts of cybersecurity. AI can find and stop threats, find strange behavior, and look at network traffic, among other things. This might be a game-changer for the industry.
2023 cybersecurity predictions that should be on your radar
How to Protect Yourself From Doxxing
If you aren’t careful online, you can become a victim of doxxing. However, you can protect yourself from being doxxed by checking your digital footprint, using a VPN and avoiding revealing any personal information online. Keep reading to learn more about the dangers of doxxing.
The Ethical Hacking Guide: Hacking for Security
Companies are under more threat than ever. The rise in cyber threats is alarming: 2021 saw a 30% increase in cyberattacks compared with 2020. Even sophisticated systems with complex countermeasure technologies for security may be vulnerable to attack. Many organizations turn to hackers to counteract these threats. Ethical hackers use the tools and methods of malicious actors to help companies pinpoint their weaknesses and build a more resilient and secure system.
Shift Left Security: How To Shift Security Left for Software Development
For a long time, security and development were two distinct aspects of programming. As organizations started to leverage software and technology as differentiating factors, the speed and quality of development became more important than ever. Organizations no longer had time after development was complete to address security vulnerabilities. Catching vulnerabilities too late opens companies up to unnecessary risk and can be costly to fix.
Leveraging Your Data to Drive Business Outcomes and Improve Cyber Resilience
It was another eventful year for security professionals in 2022. The year began on the tail of the Log4j vulnerability, data breaches were on the rise, and ransomware attacks were as prevalent as ever. So it’s safe to say cyber resilience is required to be at the forefront for public sector leaders.
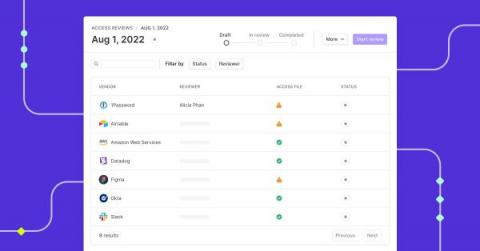
How do you perform quarterly access reviews?
Savvy organizations usually deploy some type of identity and access management (IAM) solution. IAM solutions leverage the principle of least privilege (POLP), role-based access control (RBAC), or other such mechanisms to manage access to data, applications, and IT infrastructure. However, every organization's structure and human resources capacity typically change over time as new employees are brought on board and existing ones quit.