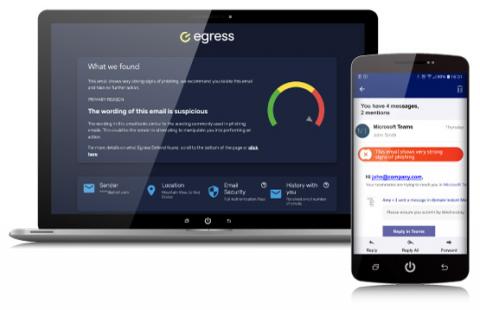
9 Ways Cyber Attackers are Looking to Exploit Government Agencies in 2023
Governments play a key role in the continued operation of society. While getting a speeding ticket or paying taxes may not be anyone’s favorite thing to do, they contribute to the government’s ability to protect its citizens while maintaining its infrastructure and services. Cybersecurity is critical for all organizations and government agencies, as they may hold sensitive information on both individuals, as well as key infrastructure.