Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Latest News
What actually is database integrity?
If you were to poll the folks in a typical office about which aspect of the infamous CIA Triad was most important to them, you would likely get different answers from different people. While confidentiality, integrity, and availability are all important and serve to function together, for the sake of fun, what if you had to choose one factor as the most critical?
Gain Advanced Endpoint Management With Certificate Manager and New Features for Enforce
Tanium can solve more of your endpoint management needs than ever before. We have just launched our new product Certificate Manager and added three new features to our core product Enforce — Modern Device Management for macOS®, Enhanced Policy Management for Windows, and USB Removable Storage Management.
Cybersecurity Learning Across Sectors - How ICCWS Brings Academics, Government, And Private Companies Together
The 18th International Conference on Cyber Warfare and Security gave researchers, policymakers, and security professionals a chance to share findings and ideas. Read the highlights.
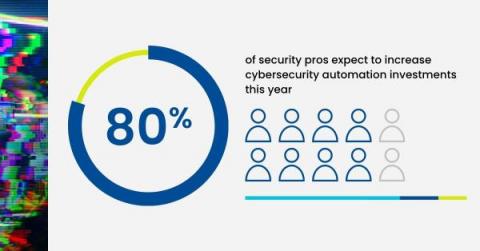
Why Security Leaders are Betting on Automation
Mass layoffs. Budget cuts. Funding shortages. Fears of recession. Headlines paint a bleak picture for organizations in 2023. To prepare for the turbulent year ahead, companies are scaling back their spending in droves. Yet, amid ruthless cost-cutting, many organizations are still prioritizing their investments in bulking up cybersecurity defenses. The question is, what are they spending these budgets on?
Why Companies Still Struggle with Least Privilege in the Cloud
Vulnerabilities are only one part of the cloud security story. Misconfigurations are still the biggest player in security incidents and, therefore, should be one of the greatest causes for concern in organizations.
Cloud Threats Memo: Cyber Espionage Campaign Using Remote Access Tools
Another day, another cyber espionage campaign exploiting two legitimate and well-known cloud services to deliver the malicious payload. Once again, this campaign was unearthed by researchers at Sentinel One, and it is aimed to distribute the Remcos Remote Access Tool (yet another example of a remote control tool used for malicious purposes) through the DBatLoader to target predominantly organizations in Eastern Europe.
Building a Secure Future: Strategies for Managing Cybersecurity in the Supply Chain
According to recent research, 68% of computer applications use open-source software libraries without the knowledge of the company. Another study by Argon Security shows that the supply chain attacks have grown up to 300% in 2021 compared to 2020.
What Can Formula 1 Teach Us About Balancing Regulation and Innovation?
Innovation and regulation are two important factors that have a significant impact on the growth of any industry, including information security. The question of whether regulation inhibits or inspires innovation is a contentious one, and there are compelling arguments on both sides.