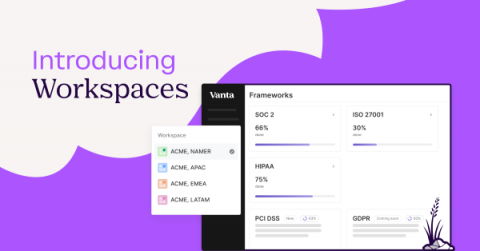
Updated Cato DLP Engine Brings Customization, Sensitivity Labels, and More
Last year, we launched Cato DLP to great success. It was the first DLP engine that could protect data across all enterprise applications without the need for complex, cumbersome DLP rules. Since then, we have been improving the DLP engine and adding key capabilities, including user-defined data types for increased control and integration with Microsoft Information Protection (MIP) to immediately apply sensitivity labels to your DLP policy. Let’s take a closer look.