Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Latest News
How To Attract Top Cyber Talent
Egnyte Celebrates Fifteen Years
Time flies when you’re building an industry-leading platform for secure content collaboration spread worldwide! July officially marks fifteen years since we filed our articles of incorporation in 2008. The co-founders of Egnyte (Vineet Jain, Rajesh Ram, Amrit Jassal, and Kris Lahiri) were actively involved in the festivities and helped to make this milestone even more memorable for employees across the globe.
What's New in Sysdig - July 2023
“What’s New in Sysdig” is back with the July 2023 edition! My name is Curtis Collicutt, based in Toronto, Canada, and the Sysdig team is excited to share our latest feature releases with you. This month, Sysdig Secure Live has been enabled for all the users!
Shift Left is Only Part of Secure Software Delivery in Financial Services
The way we manage our money has changed dramatically. In little more than a decade, we’ve gone from branch-led services to feature-rich apps offering 24/7 access to our money. Open Banking is driving product innovation, fintechs are setting a new benchmark for customer-centric experiences, and AI is taking personalization to a new level. Financial services have never been so accessible and convenient.
Attack Surface Management: Challenges, Myths, and Solutions
In the modern era of interconnectedness and digitalization, the risk of cyber threats has increased in complexity and persistence. Organizations must adopt a proactive and strategic approach to security to safeguard their assets and minimize the likelihood of cyberattacks. One essential strategy in this regard is attack surface management. It enables businesses to identify and address potential vulnerabilities and exposures comprehensively.
Monitor 1Password with Datadog Cloud SIEM
1Password is a password manager that helps organizations reduce the use of weak and reused credentials across their teams. Because your organization uses 1Password to store highly sensitive information, including passwords, access keys, and secret tokens, monitoring logs generated by activity in your 1Password environment can be useful, as unexpected patterns of behavior could indicate malicious activity by attackers.
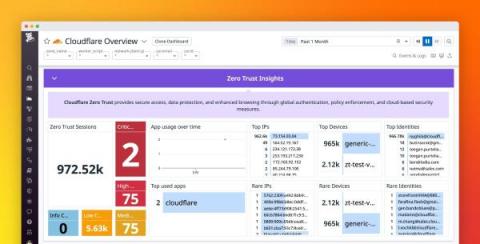
Monitor Cloudflare Zero Trust with Datadog Cloud SIEM
Cloudflare’s SASE is a zero trust network-as-a-service platform that dynamically connects users to enterprise resources, with identity-based security controls delivered close to users, wherever they are. Cloudflare spans more than 300 cities in over 100 countries, resulting in latencies under 50 milliseconds for 95 percent of the internet-connected population globally.
What is TX-RAMP? Full Compliance Guide
I have trust issues and so does my CISO
Trust is hard to earn but necessary for any successful relationship. As organizations build the systems to support Zero Trust, they find themselves balancing security and functionality across their operations. Incident Response and Network Operations in particular can be full of traumatic experiences, and as we sink into those moments the typical responses are freeze, flight, or fight.