Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Latest News
Q2 2023 Threat Landscape Report: All Roads Lead to Supply Chain Infiltrations
Kroll’s findings for Q2 2023 reveal a notable shift toward increased supply chain risk, driven not only by the CLOP ransomware gang’s exploitation of the MOVEit transfer vulnerability, but by a rise in email compromise attacks. This and other key security trends are shaping a threat landscape in which diverse cyber threats are present.
Unveiling Infra as Code Security in the GitGuardian Platform
Discover how GitGuardian's new Infra as Code Security capabilities empower cloud engineers and security professionals to detect, manage, and resolve IaC vulnerabilities precisely.
Creating a Physical Security Standard for Your Company
Cybersecurity is the pressing concern most organizations face when it comes to securing data, but not every hacker launches an attack from thousands of miles away; sometimes, the threat can walk right in through the front door to gain access to your IT system. Adversaries are not shy about using a more direct approach, which is why an organization should not overlook its physical security plan.
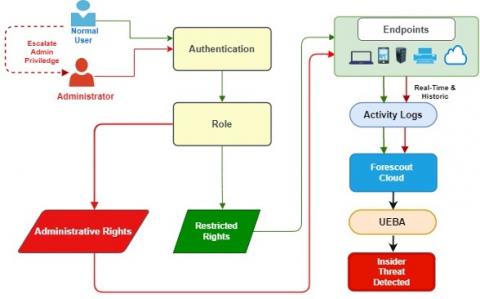
EP 34 - How to Catch a Malicious Insider w/ Eric O'Neill
Today’s episode of Trust Issues focuses on spycatching! Eric O’Neill, a former FBI counterintelligence operative and current national security strategist, joins host David Puner to discuss his legendary undercover mission to capture Robert Hanssen, one of the most notorious and damaging spies in U.S. history.
Securing Critical Infrastructures in Germany: Navigating KRITIS Regulation
Germany is widely acknowledged as one of the most technologically advanced nations. However, this prominence also implies a significant reliance on its critical infrastructures (KRITIS), which are essential to the smooth operation of the state and society. To safeguard these infrastructures, Germany has enacted new laws, IT Security Act 2.0 and KRITIS Regulation 2.0, that aim to improve the security of IT systems.
Mobile threat defense or bust
Unified endpoint management (UEM) has played a significant role over the years in enabling companies to improve the productivity and security of their corporate mobile devices and applications. In the early days of endpoint management there were separate workflows and products as it pertains to traditional endpoints, such as desktops and laptops, versus mobile devices.
Phishing Campaigns Targeting Microsoft Login Credentials Jump an Unprecedented 6100%
Monitoring of traffic to phishing pages hosted on the free hosting service Cloudflare R2 show an unheard of spike of 6100%, many going undetected by many security solutions due to the evasive techniques used. I can’t remember a time when I’ve covered a story and the reported increases were as large as the recent spike in malicious network traffic observed by Netskope.
Data Breaches Involving Social Engineering Attacks Take Longer to Identify and Contain
Continuing coverage of IBM’s recently-released Cost of a Data Breach report, we focus on the impact attacks involving social engineering have on data breach costs. There are two reports every year that we cover on this blog that you should be reading – Verizon’s Data Breach Investigations Report and IBM’s Cost of a Data Breach report. Each of these reports has been published for years, providing insight into how the state of data breaches are changing.
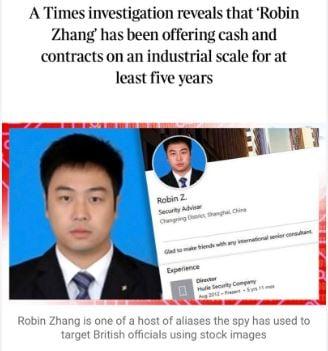
LinkedIn Deception: How a Chinese Spy Tricked Thousands of UK Officials
In last few years, cyber espionage has taken a new form. A recent investigation by The Times has unveiled a Chinese intelligence officer's extensive use of LinkedIn to target UK officials. Operating under the alias "Robin Zhang," this spy has been luring thousands of officials, scientists, and academics to hand over state secrets and sensitive technology information.