New EMEA Software Security Data Demonstrates Necessity of SCA
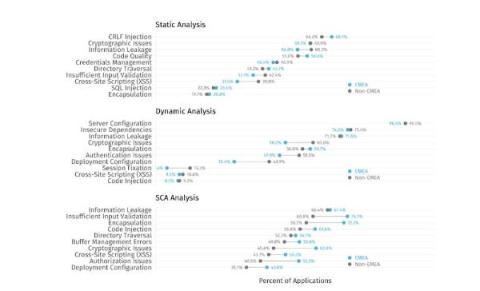
New software security data demonstrates that Software Composition Analysis (SCA) will help bolster the safety and integrity of open-source software usage for organizations in the Europe, Middle East, and Africa (EMEA) region in particular. The EU Cyber Resilience Act makes this research especially crucial and timely. Let’s dive in and look at recommendations for EMEA teams wanting to secure cloud-native development.