Between Two Alerts: Easy VPN Security Monitoring with Splunk Enterprise Security
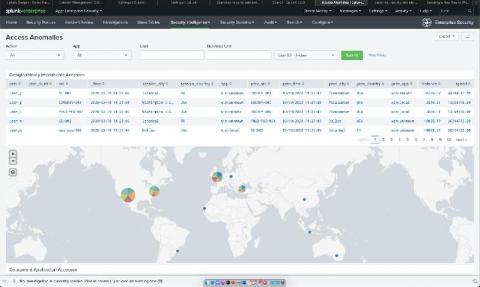
Welcome to the new world, my friends. Now that working from home is our new reality, we've found that many of our customers are taking a much closer look at the technology that binds us all together and allows us to access corporate resources: the humble VPN. In the spirit of enablement, I’ve put together a quick list of dashboards that can help add that extra bit of visibility for our faithful Splunk Enterprise Security customers.