Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Latest News
Don't let supply chain security risks poison your organization
Supply chain security risks are not new, but recent headlines are a reminder for consumers to re-examine their security practices. The story about the guy who hit his mule between the eyes with a 2×4 to “get his attention first” so the beast would then obey his gently whispered commands is memorable because it uses humor to make a serious point: Don’t wait to get clobbered before you pay attention to exhortations about what you ought to do.
CMMC vs NIST: What's the Difference?
If your firm is a government contractor working with the U.S. Department of Defense, or works anywhere in the DoD supply chain, brace for big changes in the cybersecurity requirements your business will need to meet. By 2026, the Defense Department will require its contractors to comply with new cybersecurity standards known as the Cybersecurity Maturity Model Certification — CMMC, for short.
Ransomware in 2021: What has changed? Detection and mitigation strategy
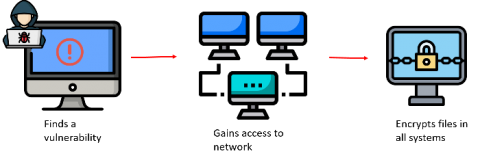
A ransomware attack is a bug that we can’t shake off. Or perhaps, it can even be called a shape-shifter that somehow finds a way into networks, no matter how many armed sentries you’ve deployed in and around your perimeter. The line between ransomware and a data breach is slowly fading. Threat actors prefer ransomware over other modes of attack because they work.
Deepfake cyberthreats - The next evolution
In 2019, we published an article about deepfakes and the technology behind them. At the time, the potential criminal applications of this technology were limited. Since then, research published in Crime Science has delved into the topic in-depth. The study identified several potential criminal applications for deepfakes. Among these categories, the following were deemed the highest risk: This list sparked the idea for this article.
Our Journey to Today
Today we came a step closer towards our ultimate vision – to empower every one of the world’s 27 million developers to develop fast while staying secure. On behalf of the entire extended Snyk family, every current and former employee, partner and customer, I’m humbled to announce that today marks another important milestone in the Snyk journey: the closing of our Series E funding round.
Detecting and mitigating Apache Unomi's CVE-2020-13942 - Remote Code Execution (RCE)
CVE-2020-13942 is a critical vulnerability that affects the Apache open source application Unomi, and allows a remote attacker to execute arbitrary code. In the versions prior to 1.5.1, Apache Unomi allowed remote attackers to send malicious requests with MVEL and OGNL expressions that could contain arbitrary code, resulting in Remote Code Execution (RCE) with the privileges of the Unomi application.
Sumo Logic to accelerate modernization of security operations with proposed acquisition of DFLabs
Actions Not Words, Demos Not Slides
In network operations, it’s never the same day twice. Most network engineers love this aspect, but it has a dark side. The best plans often fall to the wayside—in an instant work stops and firefighting begins. In the last year, I’ve been part of a whole-day colo move, diagnosed an outage in the middle of the night, and resolved a slow performance issue. I know what the networking operations experience is like, and I know how much better it can be.
Combating Risk Negligence Using Cybersecurity Culture
With a growing number of threat sources and successful cybersecurity attacks, organizations find themselves in a tricky spot if they wish to survive cyberspace. Oftentimes, the adversaries are not the challenge; the obstacle is the organization’s culture. Just like culture influences who we are as a people, culture influences the cybersecurity tone of an organization. Every organization has its own unique fit and feel.