Avoid the 3 Pitfalls of Native Database Auditing for Privileged User Monitoring
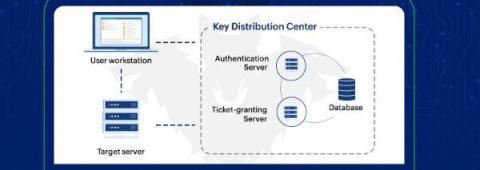
Regulations and frameworks such as PCI-DSS, SOX, NIST SP 800-53, NERC CIP and HIPAA require privileged user activity to be monitored and audited sufficiently for investigation. Privileged user monitoring and auditing for databases are critical as databases often contain the most sensitive information to an organization. Many organizations leverage built-in database auditing capabilities included with their databases to meet these monitoring and auditing requirements.