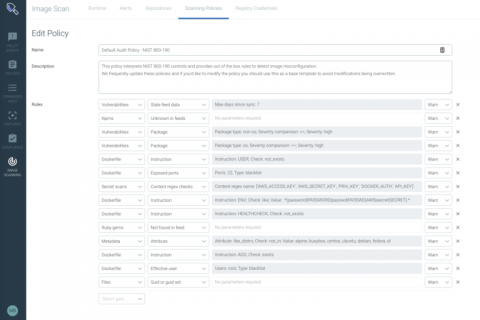
Why You Need to Align Your Cloud Strategy to Your Business Goals
Your company has decided to adopt the Cloud. Or maybe it was among the first ones that decided to rely on virtualized environments before it was even a thing. In either case, cloud security has to be managed. How do you go about that?