How Biden's Executive Order on Improving Cybersecurity Will Impact Your Systems
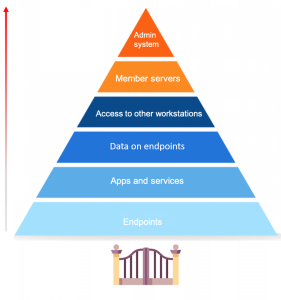
President Joe Biden recently signed an executive order which made adhering to cybersecurity standards a legal requirement for federal departments and agencies. The move was not a surprise. It comes after a string of high-profile cyber-attacks and data breaches in 2020 and 2021. The frequency and scale of these events exposed a clear culture of lax cybersecurity practices throughout both the public and private sectors.