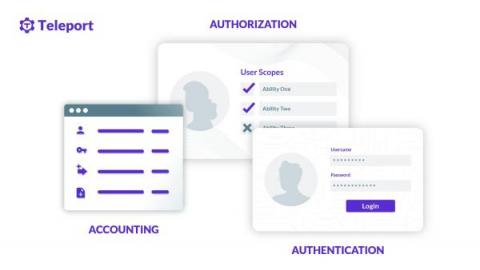
What Is AAA Security?
Authentication, authorization, and accounting, often called AAA or Triple-A, are sets of services and protocols that enable granular access control over computer networks. Before the popularity of mainstream HTTP-based authentication protocols such as OAuth and SAML, AAA protocols were the primary way to authenticate users or machines to network services.