Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Latest News
Wireless LAN Controller
Imagining a time without internet access at every point of life seems unimaginable now. The internet has been the greatest boon of the 21st century, and with wireless networking, man has progressed in leaps and bounds. It has ensured high efficiency, greater time management, increased productivity and lesser mess (no copper wires lying around). From homes to offices, students to working professionals, Wi-Fi is everyone’s go-to choice.
Why 60% of security experts are concerned about low-code/no-code apps
Last week Dark Reading released an enterprise application security survey which raised serious concerns by IT and security teams about the state of low-code/no-code applications. The survey exposed a deep lack of visibility, control and knowledge necessary to maintain the level of security maturity expected in the enterprise. In this blog post, we will look at concrete concerns raised by the survey, examine their root cause and offer recommendations on ways to address them today.
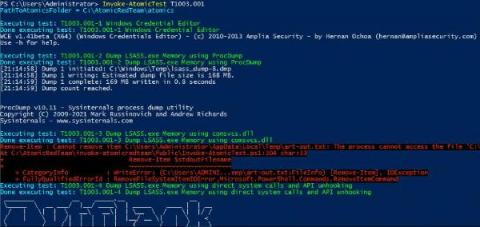
You Bet Your Lsass: Hunting LSASS Access
One of the most commonly used techniques is to dump credentials after gaining initial access. Adversaries will use one of many ways, but most commonly Mimikatz is used. Whether it be with PowerShell Invoke-Mimikatz, Cobalt Strike’s Mimikatz implementation, or a custom version. All of these methods have a commonality: targeting LSASS.
Secure your git repository with Frogbot the git bot
Introducing the newest member of the JFrog ecosystem team – Frogbot. This new git bot tool works for you by protecting your git projects, as they are being developed, from security vulnerabilities. Register for my talk “Bots to Protect your Source Code” swampUP 2022.
Training Will Be Key to Retaining SOC Analysts
Working in a Security Operations Center (SOC) is like working in an emergency room on a weekend shift at 2 AM. The steady stream of new alerts screaming for attention and combined with the lack of enough trained personnel make it a miracle that it all seems to work through on a string and a prayer. The question is though, when will the luck run out?
How to Meet the Third-party Risk Requirements of NIST CSF
The National Institute of Standards and Technology (NIST) has issued special publications focused on improving Third-Party Risk Management (TPRM) and Supply Chain Risk Management (SCRM). The NIST Cyber Security Framework (NIST CSF) special publication has become a popular option for its unique applicability to all industries with critical infrastructures. NIST CSF isn’t a light read.
How to Create Custom Cloud Security Posture Policies
Falcon Horizon, CrowdStrike’s Cloud Security Posture Management solution, uses configuration and behavioral policies to monitor public cloud deployments, proactively identify issues and resolve potential security problems. However, customers are not limited to predefined policies. This article will review the different options for creating custom cloud security posture management policies in Falcon Horizon.
What is the Most Vulnerable Data My Company Holds?
Data security is on every priority list in 2022. With the frequency of breaches never higher, many businesses assess their situation and ask cybersecurity questions. With cybersecurity policy, everything boils down to risk. Ultimately, every decision-maker wants to know, “how likely are we to be attacked?” Many believe cybercriminals only target certain kinds of data. Sensitive information, high-value financial data, and medical records are all widely accepted to carry a high risk.