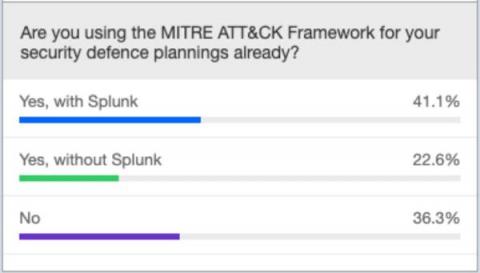
Answered: Your Most Burning Questions About Planning And Operationalizing MITRE ATT&CK
Hey There, Recently we ran a webinar ( English | German | French) in which we showed how Security Operations Teams can plan based on the MITRE ATT&CK Navigator, a threat-centric defense strategy. We also demonstrated how to operationalize it with content from the Splunk Security Essentials app via Splunk Enterprise Security. We received so many questions from attendees during the session that we weren’t able answer them all.