Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Latest News
Cybersecurity Best Practices for Small Organizations
Cyber security is an important aspect and an integral part of any online business. The layperson has little idea of what threats exist and how to protect against them. And yet, if you own a business you are almost definitely vulnerable to cyber security threats. You don’t need to be a Fortune 500 company to protect against them. By knowing what to do, you can keep your data secure and avoid breaches.
Top 7 Data Leak Detection Solutions
Today’s threat actors often carry out cyber attacks with the primary objective of accessing and exfiltrating sensitive information from your IT environment. Efforts to obtain this “crown jewel” information usually involve complex multi-phase cyber attacks. But another way in which sensitive data ends up in the hands of malicious actors with a lot less effort is when an organization exposes sensitive data assets in a data leak incident.
What cybersecurity challenges do SOCs face in the coming months?
A security operations center (SOC) is the centralized security team that deploys the tools needed to continuously monitor and improve an organization's security approach while also preventing, detecting, analyzing and responding to security alerts. You could say the SOC acts as the central command of an organization's security, bringing together its entire IT infrastructure, including its networks, devices and company data, both inside the corporate perimeter and outside.
Cybersecurity Authorities Share A List of Top Initial Access Attack Vectors
Read also: Conti threatens to overthrow the Costa Rican government, the US warns of risks of hiring North Korean tech workers, and more.
DNS Over HTTPS: Facts You Should Know
A new protocol, DNS over HTTPS (DoH), is a sensation in modern times, designed for enterprise security products and policies. A combination of DNS protocol and HTTPS protocol, DoH affects businesses, organisations, and regular users. DNS over HTTPS is used to enhance the security of network communication.
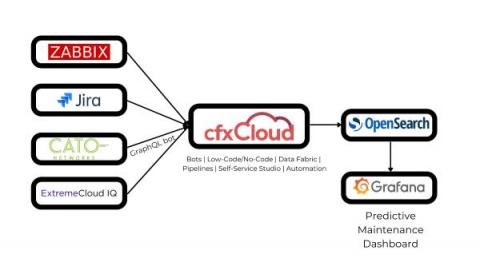
Do More with Less! Use our New GraphQL Query Bot for Cato Networks, Monday.Com, and More
Interactive Phishing: Using Chatbot-like Web Applications to Harvest Information
Phishing website links are commonly delivered via email to their respective targets. Once clicked, these websites often show a single webpage that outright asks for sensitive information like account login credentials, credit card details, and other personally identifiable information (PII). Recently, we have encountered an interesting phishing website containing an interactive component in it: a chatbot.
Top 10 Mobile App Security Questions Answered
With the rise of internet penetration and increased mobile usage, the significance of mobile applications has increased multifold. Everything is covered through mobile applications, from mundane day-to-day activities to high-end financial transactions. According to Techjury, there are 10 billion mobile devices currently in use, and a staggering more than 51% of people in the USA spend their time on mobile phones.
Security Ratings Recognized in NIST Cyber Supply Chain Risk Management Update
On May 5, 2022, the National Institutes of Standards and Technology (NIST) formally recognized outside-in third party security ratings and vendor risk assessment in their update to Special Publication 800-161. This update to federal standards specifically cites security ratings as a “foundational capability that "provide 14028." NIST SP 800-161 was designed to standardize supply chain risk management best practices for federal agencies and industry.