Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Latest News
How Tech Innovation is Revolutionising Cybersecurity for Law Firms
Performance improvements, snappier ports, and spring cleaning
The vulnerabilities page allows you to see all findings across your attack surface. This includes simple filters that let you specify what you want to focus on, including the level of severity, which domains you want to look at, and whether it was found in the past week or the past month.
What is the HIPAA Security Rule?
Title II of the Health Insurance Portability and Accountability Act of 1996 (HIPAA) has two key provisions: the Privacy Rule and the HIPAA Security Rule. The Privacy Rule establishes standards for protecting certain health information, or PHI. The Privacy Rule requires those organizations that are governed by HIPAA (covered entities) to implement safeguards to protect the privacy of PHI, and gives individuals the right to access and share their health records.
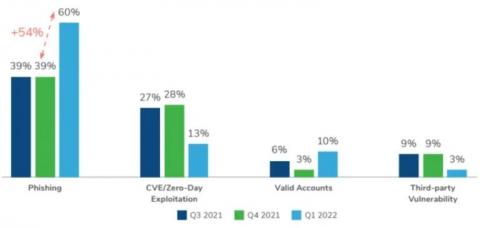
New Kroll threat landscape report reveals threat actors targeting email for access and extortion
How DNS filtering can help protect your business from Cybersecurity threats
The Domain Name System (DNS) is an important tool that connects devices and services together across the Internet. Managing your DNS is essential to your IT cybersecurity infrastructure. When poorly managed, DNS can become a huge landscape for attackers. Nonetheless, when properly configured, DNS is a key line of defense against cyber threats for your organization. DNS filtering is an essential component of business cybersecurity.
Securing Your MongoDB Database
Securing databases is a significant aspect of an organization’s infrastructure and security practices. This article explores the methodologies and steps for securing MongoDB Database, a popular non-relational, flexible, and document-oriented database. Before starting, you should understand the difference between self-hosted MongoDB and MongoDB Atlas.
Cyberattacks Targeting NFT Marketplaces and Cryptographic Aficionados
Everything technology touches gets a digital makeover and the creative space wouldn’t be the exception. Non-fungible tokens (NFTs) are virtual assets that represent objects influenced by art, music, games, and videos. You can only buy them online, likely with cryptocurrency. NFTs are generally encoded with the same underlying software as many cryptos. In fact, they are part of the Ethereum blockchain, a cryptocurrency, like bitcoin or dogecoin.
Why Web Application Visibility Is Important to JavaScript Security
Web application visibility is all about the insight and control application security professionals have into the software operating on the front end or client side. Sitting down to write about why web application visibility is important to JavaScript security, I was reminded of a folk song about coding that was popular back in the 1980s. (Yes, you read that right. A popular folk song about coding. Fans of Stan Rogers or listeners of the cult-favorite, syndicated radio show known as Dr.
How to Use SIEM Tools in the Modern World
In our highly connected world, organizations of all sizes need to be alert to the risk of cyberattacks. The genuine threats to today’s enterprises include data leaks, ransomware, and theft of commercial secrets or funds, with the potential for severe financial and reputational damage. Investing in tools to monitor your systems and alert you to suspicious activity as early as possible is vital for strengthening your security posture.